Cyber Security
-


SOC
-


EDR/XDR
-


XOAR & SIEM
-


Network Security
-


Zero Trust Security
-


Data Governance, Risk and Compliance
-


Managed Response & Detection
-


Digital Forensics
-

IoT Security
-


VAPT
-


Cyber for Citizens
Cybersecurity Solutions
Cyber security solutions are technological tools and services that help protect organizations against cyber-attacks, which can result in application downtime, theft of sensitive data, damage to reputation, compliance fines, and other adverse consequences.
SOC
If you are a small or mid-sized business with an average network security plan, you are 70% more likely to be hacked and have a 50% chance of losing your business. Small and mid-sized businesses are considered soft or easy targets and an attack can cost the company anywhere between $120,000 – $2 million. Unfortunately, most businesses that have been attacked shut down within 6 months of a cyber-attack.
An organization's information security is monitored, assessed, and maintained by a security operations center (SOC), which offers these capabilities as a service. The SOC serves as the company's intelligence hub, gathering information in real-time from its networks, servers, endpoints, and other digital assets while utilizing intelligent automation to recognize, prioritize, and address potential cybersecurity threats.
CBT now offers our in-house SOC services. Get threat detection and alerting abilities of Security Information & Event Management (SIEM), 24×7 Network Monitoring of your network infrastructure and detection of anomalous employee activity with Data Leakage Prevention, all in one Box. This aims to reduce staff requirements, remove redundancies and lower your cost of a breach by transferring risk.
Cloud Box Technologies SOC services which are managed by subject specialists act as an extension of your team performing 24/7 cybersecurity operations using best-of-breed technologies to safeguard your business from attacks and respond to incident
EDR/XDR
Endpoint security is the practice of preventing malicious actors and campaigns from exploiting endpoints or entry points of end-user devices such as desktops, laptops, and mobile devices. Endpoint security systems guard against cybersecurity threats on a network or in the cloud. Endpoint security has progressed from simple antivirus software to comprehensive protection against sophisticated malware and evolving zero-day threats.
Nation-states, hacktivists, organized crime, and malicious and unintentional insider threats pose a threat to organizations of all sizes. Endpoint security is frequently regarded as the frontline of cybersecurity, and it is one of the first places organizations look to secure their enterprise networks.
As the volume and sophistication of cybersecurity threats has increased, so has the demand for more sophisticated endpoint security solutions. Endpoint protection systems are now designed to detect, analyze, block, and contain ongoing attacks. To accomplish this, they must work together as well as with other security technologies to provide administrators with visibility into advanced threats in order to accelerate detection and remediation response times.


What is XDR?
Extended Detection and Response (XDR) represents a revolutionary approach to threat detection and response. It is a cloud-native, vendor-specific solution that seamlessly integrates various security products into a unified security operations system. Forrester Research defines XDR as the evolution of EDR, optimizing real-time threat detection, investigation, response, and hunting.
Key Features of XDR:
Unified Security: XDR consolidates security-relevant endpoint detections with telemetry from network analysis, email security, identity and access management, cloud security, and more.
Proactive Threat Detection: XDR provides a proactive stance against hidden, stealthy, and sophisticated threats by applying analytics and automation to all organizational data.
Cross-Source Threat Tracking: With XDR, cybersecurity teams can track threats across any source or location within the organization, ensuring comprehensive coverage.
Enhanced Productivity: XDR increases the efficiency of security operations, allowing teams to conclude investigations more swiftly and get more out of their security investments.
Strengthening Business Security with EDR and XDR
Actor(s):
Users: Employees and stakeholders involved in the business operation.
Cybersecurity Teams: Responsible for monitoring and responding to security incidents.
Trigger:
Cybersecurity Threat: The detection of a potential cybersecurity threat targeting the business operation.
Preconditions:
The EDR and XDR solutions are properly installed and configured on all business devices.
Cybersecurity teams have access to real-time threat intelligence feeds.
Regular system updates and patches are in place.
Main Flow of Events:
Detection:
EDR identifies suspicious activity on individual devices.
XDR consolidates information from EDR, network analysis, email security, and other sources to assess the scope of the threat.
Alert Notification:
Cybersecurity teams receive alerts about the detected threat.
EDR provides details on the endpoint-specific nature of the threat.
XDR offers insights into the broader context of the threat across various channels.
Investigation:
Cybersecurity teams conduct a detailed investigation to understand the nature and severity of the threat.
EDR and XDR assist in correlating data and identifying potential attack vectors.
Response:
Based on the investigation, cybersecurity teams initiate a targeted response to neutralize the threat.
EDR and XDR work in tandem to implement containment measures and prevent further spread.
Resolution:
The threat is successfully neutralized, and systems are restored to a secure state.
EDR and XDR continue monitoring for any residual threats or potential vulnerabilities.
Advanced Threat Scenario:
If the threat is identified as advanced or sophisticated, additional security measures are activated.
EDR and XDR collaborate to implement advanced threat hunting techniques.
False Positive:
In the case of a suspected threat turning out to be a false positive, EDR and XDR assist in quickly confirming the error and adjusting alert thresholds.
Postconditions:
All business devices remain secure from the detected threat.
Cybersecurity teams have a comprehensive understanding of the incident.
EDR and XDR continue to provide ongoing monitoring and protection against future threats.
In conclusion, this use case showcases the systematic interaction between users, cybersecurity teams, and advanced security solutions (EDR and XDR) in responding to and mitigating a cybersecurity threat in a generic business operation. The proactive approach ensures the security of sensitive data, maintains operational continuity, and fosters a resilient cybersecurity strategy for the organization.
XOAR & SIEM
Security orchestration, automation, and response (SOAR) and security, information, and event management (SIEM) are cybersecurity tools that collect data to help IT security professionals protect a business’s network environment from cyber threats and vulnerabilities. Both SOAR and SIEM collect log and event data from applications and network devices, but each solution handles threats differently.
The purpose of SOAR and SIEM is to identify and mitigate any potential cyberattacks by taking specific actions to resolve and eliminate any cyber threats or vulnerabilities.
SOAR can be integrated with diverse IT systems and devices using application programming interfaces (APIs) to collect data. For example, SOAR can retrieve data from endpoint protection tools, firewalls, intrusion detections systems, and SIEM platforms. A SOAR platform collects data from multiple disparate IT devices and applications and takes a specific action using predictive analysis to avert a threat before it happens.
Comparatively, SIEM collects log and event data from server applications, network devices, and infrastructure components that can become security alerts on a centralized platform. This provides real-time analysis and security monitoring by a team of IT security professionals to investigate.
SOAR tools are more robust with automated workflows that mitigate threats and make SecOps teams more efficient. However, a SOAR platform depends on SIEM data to effectively evaluate, validate, and respond to credible threats.
Both cybersecurity solutions effectively identify threats and vulnerabilities but have different resolution approaches. The best cybersecurity strategy for most businesses is one that leverages both solutions.

Network Security
Network security is a broad concept that encompasses a wide range of technologies, devices, and processes. It is a set of rules and configurations that use both software and hardware technologies to protect the integrity, confidentiality, and accessibility of computer networks and data. Every organization, regardless of size, industry, or infrastructure, requires network security solutions to protect it from the ever-changing landscape of cyber threats in the wild today.
Today's network architecture is complex, with a constantly changing threat environment and attackers constantly looking for and exploiting vulnerabilities. These flaws can exist in a variety of contexts, including devices, data, applications, users, and locations. As a result, many network security management tools and applications are now in use to address individual threats and exploits as well as regulatory non-compliance. When a few minutes of downtime can cause widespread disruption and massive damage to an organization's bottom line and reputation, these safeguards are critical.
Any organization that works with networked data and systems should prioritize network security. Network security can not only protect assets and data integrity from external attacks, but it can also manage network traffic more efficiently, improve network performance, and ensure secure data sharing between employees and data sources.
There are numerous tools, applications, and utilities available to assist you in protecting your networks from attack and downtime. Forcepoint provides a suite of network security solutions that centralize and simplify often complex processes while also ensuring robust network security across your enterprise.
Zero Trust Security
Zero Trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data. Zero Trust assumes that there is no traditional network edge; networks can be local, in the cloud, or a combination or hybrid with resources anywhere as well as workers in any location.
Zero Trust is a framework for securing infrastructure and data for today’s modern digital transformation. It uniquely addresses the modern challenges of today’s business, including securing remote workers, hybrid cloud environments, and ransomware threats. While many vendors have tried to create their own definitions of Zero Trust, there are a number of standards from recognized organizations that can help you align Zero Trust with your organization.
Execution of this framework combines advanced technologies such as risk based multi-factor authentication, identity protection, next-generation endpoint security, and robust cloud workload technology to verify a user or systems identity, consideration of access at that moment in time, and the maintenance of system security. Zero Trust also requires consideration of encryption of data, securing email, and verifying the hygiene of assets and endpoints before they connect to applications.


Zero Trust is a significant departure from traditional network security which followed the “trust but verify” method. The traditional approach automatically trusted users and endpoints within the organization’s perimeter, putting the organization at risk from malicious internal actors and legitimate credentials taken over by malicious actors, allowing unauthorized and compromised accounts wide-reaching access once inside. This model became obsolete with the cloud migration of business transformation initiatives and the acceleration of a distributed work environment due to the pandemic that started in 2020.
Zero Trust architecture therefore requires organizations to continuously monitor and validate that a user and their device has the right privileges and attributes. It also requires enforcement of policy that incorporates risk of the user and device, along with compliance or other requirements to consider prior to permitting the transaction. It requires that the organization know all of their service and privileged accounts and can establish controls about what and where they connect. One-time validation simply won’t suffice because threats and user attributes are all subject to change.
As a result, organizations must ensure that all access requests are continuously vetted prior to allowing access to any of your enterprise or cloud assets.
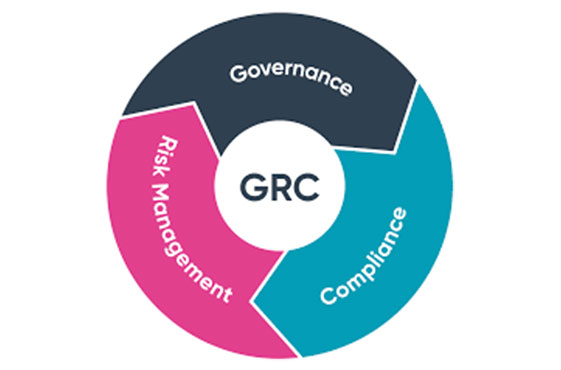
Data Governance, Risk and Compliance
Governance, Risk, and Compliance (GRC) is a structured way to align IT with business goals while managing risks and meeting all industry and government regulations. It includes tools and processes to unify an organization's governance and risk management with its technological innovation and adoption. Companies use GRC to achieve organizational goals reliably, remove uncertainty, and meet compliance requirements. Most businesses are familiar with these terms but have practiced them separately in the past. GRC combines governance, risk management, and compliance in one coordinated model. This helps your company reduce wastage, increase efficiency, reduce noncompliance risk, and share information more effectively.

Governance
A company's governance is the set of policies, rules, or frameworks that it uses to achieve its business objectives. It specifies the roles and responsibilities of key stakeholders like the board of directors and senior management. Good corporate governance, for example, assists your team in incorporating the company's social responsibility policy into their plans.
Good governance includes the following:
1. Ethics and accountability
2. Transparent information sharing
3. Conflict resolution policies
4. Resource management
Risks that businesses face include financial, legal, strategic, and security risks. Proper risk management assists businesses in identifying these risks and determining how to mitigate any that are discovered. An enterprise risk management program is used by businesses to predict potential problems and minimize losses. For example, you can use risk assessment to identify and close security gaps in your computer system.
Compliance
Compliance is the act of following rules, laws, and regulations. It applies to industrial bodies' legal and regulatory requirements, as well as internal corporate policies. Compliance in GRC entails implementing procedures to ensure that business activities are in accordance with the applicable regulations. Healthcare organizations, for example, must follow laws like HIPAA that protect patients' privacy.
By implementing GRC programs, businesses can make better decisions in a risk-aware environment. An effective GRC program helps key stakeholders set policies from a shared perspective and comply with regulatory requirements. With GRC, the entire company comes together in its policies, decisions, and actions.
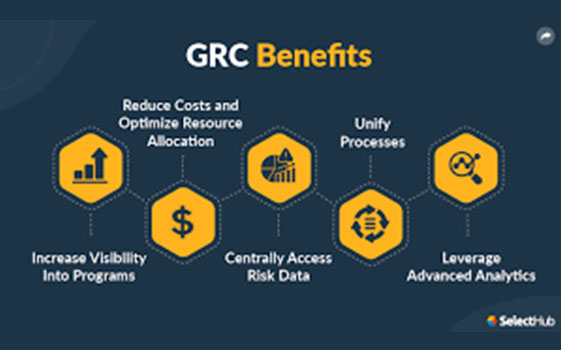
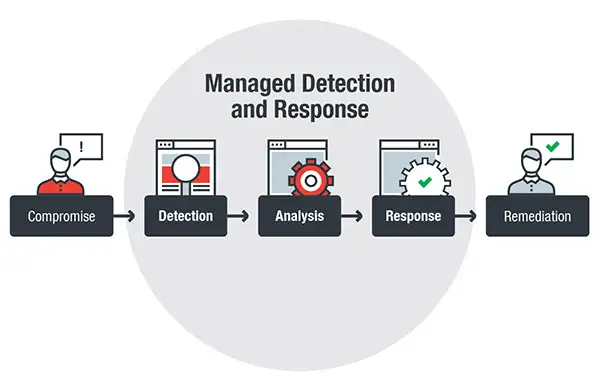
Managed Response & Detection
Managed detection and response (MDR) provides an organization with the tools that it needs to effectively protect itself from cyber threats. By partnering with an MDR provider, an organization gains access to a 24/7 security operations center (SOC) and the security expertise necessary to effectively protect the organization. MDR goes beyond simply trying to stop an ongoing attack and works to ensure that an organization will never have to worry about being impacted by the same cyberattack twice.
Managed detection and response is a category of a Security-as-a-Service offering, where an organization outsources some of its security operations to a third-party provider. As its name suggests, it goes beyond simply detecting threats to actually working to remediate them on an organization’s network.


An MDR Security service offering typically includes a few different features:
- Incident Investigation: MDR Security service providers will investigate an alert and determine whether it is a true incident or a false positive. This is accomplished through a combination of data analytics, machine learning, and human investigation.
- Alert Triage: Not all security incidents are created equal, and a number of factors can impact the priority of different events. An MDR provider will organize the list of security events, enabling the most critical to be handled first.
- Remediation: A Managed Detection and Response provider will offer incident remediation as a service. This means that they will remotely take action to respond to a security event within a customer’s network.
- Proactive Threat Hunting: Not all security incidents are caught by an organization’s security stack. Managed Detection and Response providers will proactively search an organization’s network and systems for indications of an ongoing attack and, if one is detected, take steps to remediate it.
Digital Forensics
Digital forensics is the process of storing, analyzing, retrieving, and preserving electronic data that may be useful in an investigation. It includes data from hard drives in computers, mobile phones, smart appliances, vehicle navigation systems, electronic door locks, and other digital devices. The process's goal of digital forensics is to collect, analyze, and preserve evidence.
The process involves Identification, preservation, analysis, documentation and presentation. The process aids in the recovery, analysis, and preservation of computers and related materials for the investigating agency to present them as evidence in a court of law. It aids in determining the motive for the crime and the identity of the primary perpetrator. Creating procedures at a suspected crime scene to help ensure that the digital evidence obtained is not tainted. Data acquisition and duplication: The process of recovering deleted files and partitions from digital media in order to extract and validate evidence. Assists you in quickly identifying evidence and estimating the potential impact of malicious activity on the victim. Creating a computer forensic report that provides comprehensive information on the investigation process. Keeping the evidence safe by adhering to the chain of custody

IoT Security
An Internet of Things device is any network-connected physical asset that is not a computer. While traditional network security technology and protocols are used by enterprise IT teams to protect standard IT devices, the security risks associated with IoT devices are less well-known, and securing IoT is an unaddressed challenge in many organizations. Standard cybersecurity systems are incapable of recognizing and identifying specific types of IoT devices, as well as the distinct risk profiles and expected behaviors that go with them.
Furthermore, IoT devices can be deployed by any business center, circumventing traditional network security controls and processes. Printers, cameras, sensors, lighting, HVAC, appliances, infusion pumps, handheld scanners (and the list goes on) are all network-connected IoT devices that use different hardware, chipsets, operating systems, and firmware that introduce vulnerabilities and risk.
IoT security can be defined as a cybersecurity strategy and protection mechanism that protects against cyberattacks that specifically target physical IoT devices connected to the network. Without strong security, any connected IoT device is vulnerable to breach, compromise, and control by a bad actor, allowing them to eventually infiltrate, steal user data, and bring systems down.
The overarching challenge for IoT security is that as large numbers of diverse IoT devices continue to connect to the network, the attack surface expands dramatically in parallel. Finally, the overall network security posture is reduced to the level of integrity and protection provided by the least secure device.
Strategically minded CISOs and security leaders are moving beyond legacy network security solutions and taking a complete IoT lifecycle approach, creating an IoT security posture that reliably enables IoT innovation and protects the network from existing and unknown threats. The lifecycle approach encompasses five critical stages of IoT security.
Network security and operations teams should be incorporating IoT security into standard practice, process and procedure to ensure both managed and unmanaged devices fall within the same level of visibility and control across the IoT security lifecycle:
• Identify all managed and unmanaged devices with context.
• Accurately assess and identify vulnerabilities and risks associated with all devices.
• Automate Zero Trust policies and enforcement of those policies.
• Take swift action on preventing known threats.
• Rapidly detect and respond to unknown threats.
An effective strategy for security in IoT must protect devices and the networks they are connected to from the ever-widening spectrum of IoT security risks.

VAPT
Vulnerability Assessment and Penetration Testing (VAPT) is a term used to describe security testing that is designed to identify and help address cyber security vulnerabilities. The meaning of VAPT can vary from one geographical region to another, either as a bracket for multiple distinct services, or a single, combined offering. VAPT as a whole could include anything from automated vulnerability assessments to human-led penetration testing and EDR operations.
VAPT describes a broad range of security assessment services designed to identify and help address cyber security exposures across an organization’s IT estate.
To ensure that you choose the right type of assessment for your company’s needs, it’s important to understand the various types of VAPT services and the differences between them. The diverse nature of VAPT assessments means that they can vary significantly in depth, breadth, scope and price, so this understanding is critical to ensure tests deliver the best value for money.


The evolving tools, tactics and procedures used by cybercriminals to breach networks means that it’s important to regularly test your organization’s cyber security.
VAPT helps to protect your organization by providing visibility of security weaknesses and guidance to address them. VAPT is increasingly important for organizations wanting to achieve compliance with standards including the GDPR, ISO 27001 and PCI DSS.
Cyber for Citizens
Cyber security is the means by which individuals and organizations reduce the risk of being affected by cybercrime.
Cyber security's core function is to protect the devices we all use (smartphones, laptops, tablets and computers), and the services we access online - both at home and work - from theft or damage. It's also about preventing unauthorized access to the vast amounts of personal information we store on these devices, and online.
Cyber security is important because smartphones, computers and the internet are now such a fundamental part of modern life, that it's difficult to imagine how we'd function without them. From online banking and shopping, to email and social media, it's more important than ever to take steps that can prevent cyber criminals getting hold of our accounts, data, and devices.
CBT proudly brings a unique offering of cybersecurity for individuals to help mitigate any potential threats to your personal data or tech.


